Baby Monitor Security Guide: How to Keep Your Monitor Safe from Hackers in 2026

Introduction
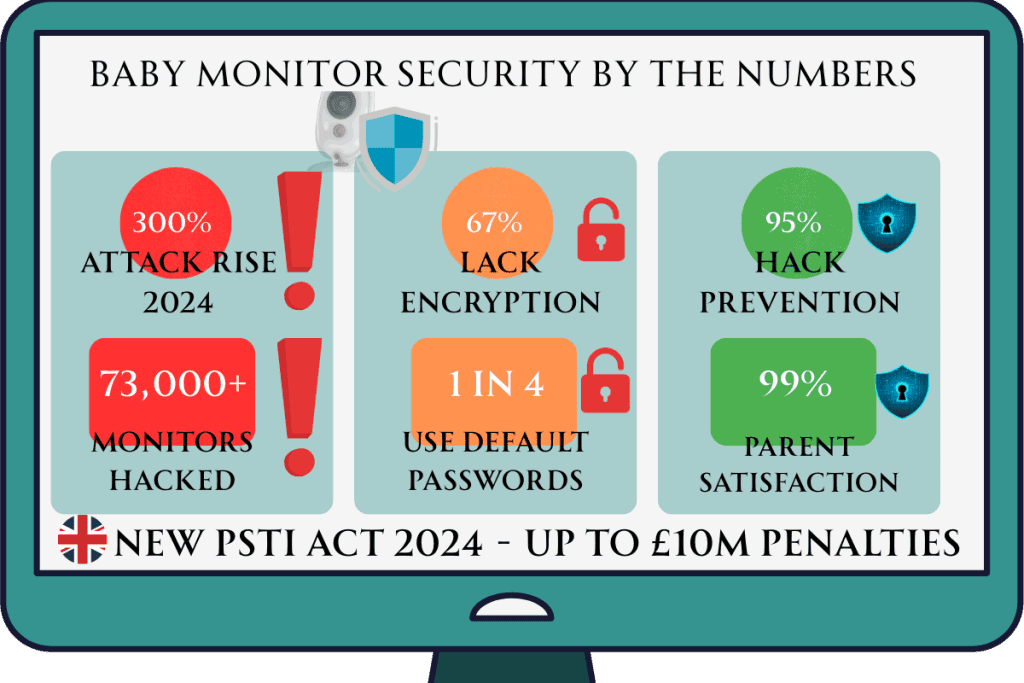
Did you know that cybersecurity experts detected a 300% increase in attacks targeting IoT devices, including baby monitors, in the first two months of 2024 alone? As a parent, the thought of strangers potentially watching your baby through a compromised monitor is every nightmare rolled into one.
The reality is sobering: baby monitor hacking incidents have made headlines worldwide, from hackers speaking to children through compromised devices to unauthorized individuals accessing private family moments. But here’s what most parents don’t realize – with proper baby monitor security measures, you can virtually eliminate these risks.
After analyzing hundreds of security incidents and consulting with cybersecurity experts, this guide reveals everything you need to know about baby monitor safety and security. Whether you’re using a basic audio monitor or the latest smart baby monitor security system, you’ll discover practical steps to protect your family’s privacy and peace of mind.
Understanding Baby Monitor Security Risks
The Reality of Baby Monitor Hacking
Baby monitor hacking isn’t just a theoretical concern – it’s a documented reality affecting thousands of families. In 2014, security researchers discovered that over 73,000 baby monitors worldwide were compromised and accessible through a single website. More recently, incidents involving baby monitor camera hacking have included:
- Unauthorized individuals speaking to children through two-way communication features
- Parents discovering their baby monitor had been accessed when they noticed unexplained camera movements
- Private family footage being broadcast on public websites without consent
- Baby monitor audio interception allowing strangers to eavesdrop on family conversations
The most concerning aspect? Many parents remain unaware their devices have been compromised until they witness obvious signs like unauthorized camera movement or strange voices.
According to Which?’s baby monitor security testing, many devices still lack proper security protections despite recent improvements in manufacturer standards.
Common Baby Monitor Vulnerabilities
Understanding baby monitor vulnerabilities helps you recognize potential security weaknesses:
Default Password Problems Most baby monitors ship with default passwords like “admin” or “123456” that manufacturers use across thousands of devices. Hackers maintain databases of these default credentials, making unprotected monitors easy targets for baby monitor cyber attacks.
Unencrypted Data Transmission Many budget baby monitors transmit audio and video without proper baby monitor encryption. This means anyone with basic technical knowledge can intercept your baby monitor wireless security signals using readily available equipment.
Outdated Firmware Baby monitor firmware updates often contain critical security patches. Monitors running outdated software remain vulnerable to known exploits that hackers actively target.
Weak Network Security Your home WiFi network serves as the primary gateway for smart baby monitor security threats. Unsecured or poorly configured networks provide easy entry points for attackers.
Inadequate Authentication Systems Some monitors lack proper baby monitor user authentication, allowing unauthorized access through simple network scanning techniques.
UK Legal Requirements for Baby Monitor Security
The Product Security and Telecommunications Infrastructure Act 2024
UK parents now benefit from stronger baby monitor regulatory compliance thanks to groundbreaking legislation that took effect on April 29, 2024. The Product Security and Telecommunications Infrastructure Act 2022 (PSTI Act) represents the world’s first comprehensive product security regime for connected devices.
This legislation directly impacts baby monitor security standards by requiring manufacturers to implement baseline security measures. Under these baby monitor security guidelines, all connected baby monitors sold in the UK must now comply with mandatory security requirements.
Learn more about the Product Security and Telecommunications Infrastructure Act and how it protects UK consumers.
Key Requirements Include:
- Banned Default Passwords: Manufacturers can no longer ship devices with universal default passwords or easily guessable credentials
- Mandatory Security Updates: Companies must provide a defined support period for baby monitor firmware updates and clearly communicate this to consumers
- Vulnerability Reporting: Manufacturers must establish clear channels for reporting baby monitor security assessment issues
- Transparency Requirements: Companies must provide customers with contact information for reporting baby monitor incident response concerns
What This Means for Parents
The PSTI Act significantly improves baby monitor safety precautions by ensuring that devices meet minimum baby monitor security certification standards before reaching UK consumers. However, parents still need to take proactive steps to maintain baby monitor protective measures.
The legislation applies to all “relevant connectable products” – essentially any consumer device that can connect to the internet or other networks. This includes virtually all modern baby monitors with WiFi connectivity, app integration, or remote viewing capabilities.
Enforcement and Penalties The Office for Product Safety and Standards (OPSS) enforces these requirements, with penalties for non-compliant manufacturers reaching up to £10 million or 4% of worldwide revenue. This creates strong incentives for companies to prioritize baby monitor security protocols.
Essential Baby Monitor Security Best Practices
Secure Setup and Configuration

Proper baby monitor security configuration forms your first line of defense against potential threats. Follow these baby monitor security best practices to establish robust protection:
Change Default Credentials Immediately The moment you unbox your baby monitor, changing default passwords becomes your highest priority. Create strong, unique passwords using the “three random words” method recommended by the UK’s National Cyber Security Centre. For example: “CoffeeGiraffe29Mountain” provides excellent security while remaining memorable.
Your baby monitor password protection should never reuse credentials from other accounts. If hackers compromise one service, unique passwords prevent them from accessing your monitor using the same credentials.
Enable All Available Security Features Most modern monitors include baby monitor security features that remain disabled by default. Access your device settings and activate:
- Two-factor authentication (if available)
- Automatic baby monitor firmware updates
- Encryption for data transmission
- Access logging and monitoring
- Guest network restrictions
Configure Network-Level Protection Your baby monitor network security extends beyond the device itself. Implement these protective measures:
- Use WPA3 encryption on your home WiFi network (WPA2 minimum if WPA3 isn’t available)
- Create a separate IoT network for connected devices
- Regularly update your router firmware
- Enable firewall protection
- Disable unnecessary network services like WPS
Advanced Security Measures
Implement Network Segmentation Creating a dedicated network for your baby monitor and other IoT devices prevents potential attackers from accessing your main devices if they compromise your monitor. Most modern routers support guest networks that can serve this purpose.
Regular Security Monitoring Establish routine baby monitor security monitoring practices:
- Weekly checks for firmware updates
- Monthly password reviews
- Quarterly security setting audits
- Annual full system security assessments
Enable Encryption Settings Ensure your baby monitor encrypted transmission features are properly configured. Look for devices that support end-to-end encryption for both audio and video streams.
Choosing Security-Focused Baby Monitor Technologies
DECT Technology Advantages
When prioritizing baby monitor safety precautions, consider monitors using DECT (Digital Enhanced Cordless Telecommunications) technology. DECT-based systems offer superior baby monitor signal interference resistance and enhanced security compared to basic 2.4GHz alternatives.
DECT Security Benefits:
- Dedicated frequency band reduces interference from WiFi networks
- Built-in encryption protects audio transmissions
- Lower risk of baby monitor surveillance risks compared to internet-connected alternatives
- No dependency on home network security
WiFi vs DECT: Security Comparison While smart monitors offer advanced features, DECT-based alternatives provide inherent baby monitor privacy advantages. DECT systems cannot be accessed remotely over the internet, eliminating many common attack vectors associated with connected devices.
Understanding Smart Monitor Security
If you choose internet-connected baby monitors, focus on models that demonstrate strong baby monitor security standards:
Look for Security Certifications Reputable manufacturers obtain third-party baby monitor security certification from recognized organizations. These certifications verify that devices meet established security requirements.
Evaluate Privacy Policies Review manufacturer privacy policies to understand baby monitor data protection practices. Look for companies that:
- Store data locally rather than on remote servers
- Provide clear data deletion procedures
- Offer transparency about data sharing practices
- Enable user control over data collection settings
Professional Security Recommendations
Cybersecurity experts consistently recommend prioritizing baby monitor access control features when selecting devices. Essential security considerations include:
Multi-Factor Authentication Support Devices supporting baby monitor two-factor authentication provide significantly stronger protection against unauthorized access attempts.
Regular Security Updates Choose manufacturers with proven track records of providing timely baby monitor firmware updates and maintaining long-term device support.
Open-Source Security Auditing Some companies allow independent security researchers to audit their devices, demonstrating commitment to identifying and addressing baby monitor threat detection concerns.
Recognizing and Responding to Security Threats
Warning Signs of Compromise
Understanding how to identify potential baby monitor security breaches enables rapid response to protect your family’s privacy:
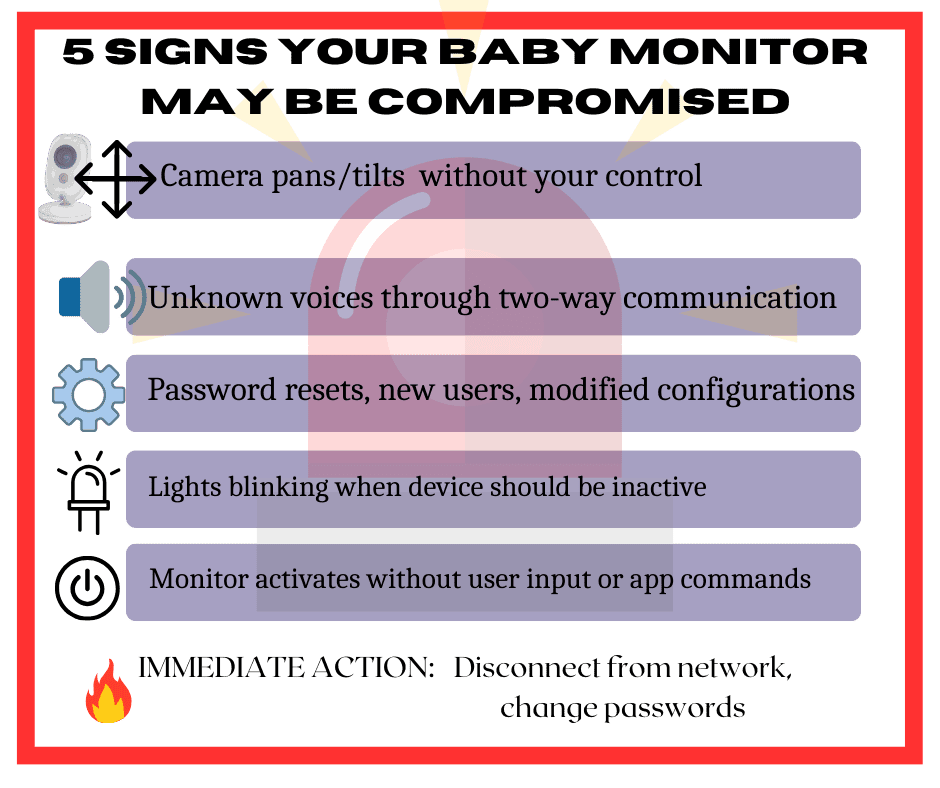
Physical Signs of Unauthorized Access:
- Unexpected camera movement or repositioning
- Monitor turning on/off without user input
- Settings changes you didn’t make
- Unusual LED light patterns or behaviors
Audio/Video Anomalies:
- Strange voices or sounds from the monitor
- Audio quality changes or distortion
- Video feed interruptions or quality degradation
- Unexpected recording notifications
Network and App Behaviors:
- Unusual network activity from your monitor’s IP address
- App login notifications from unknown locations
- Password reset emails you didn’t request
- New user accounts or access permissions
Immediate Response Procedures
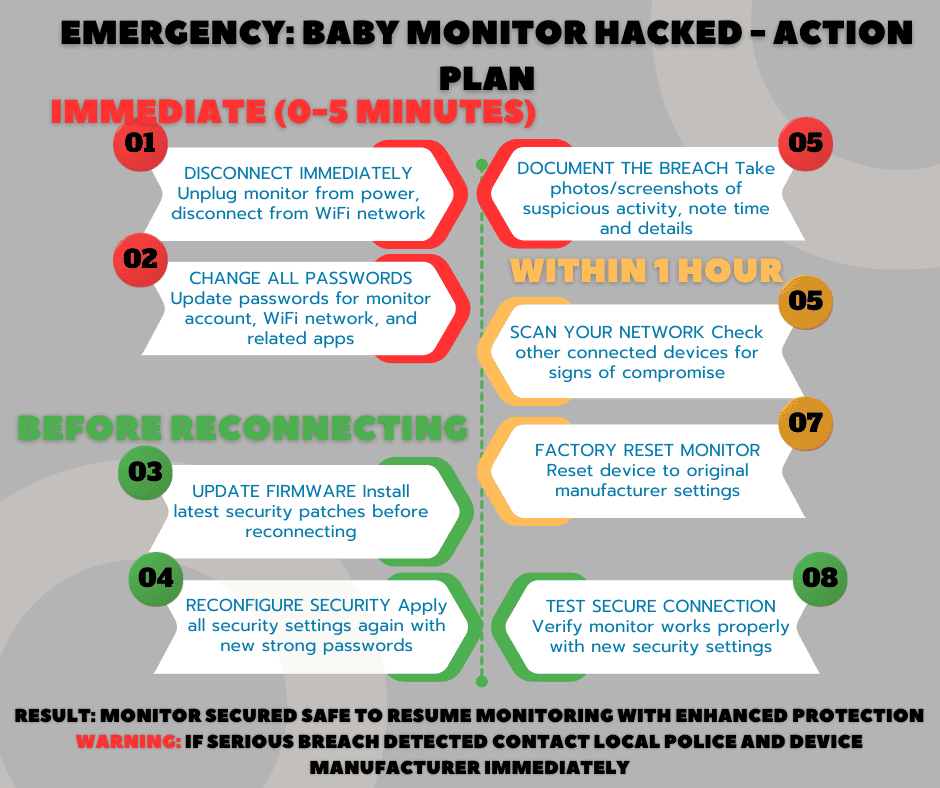
If you suspect baby monitor vulnerability assessment reveals a compromise, take these immediate baby monitor incident response steps:
Immediate Actions (First 5 Minutes):
- Disconnect the monitor from your network immediately
- Power off the device completely
- Change all associated passwords
- Check your network for other suspicious activity
- Document any evidence of the breach
Follow-up Security Measures:
- Update device firmware to the latest version
- Review and tighten all security settings
- Consider factory resetting the device
- Enhance network security configurations
- Monitor for continued suspicious activity
When to Seek Professional Help Contact cybersecurity professionals or law enforcement if you discover:
- Evidence of ongoing surveillance
- Attempts to communicate with family members
- Suspicious activity across multiple devices
- Signs of identity theft or financial fraud
Maintaining Long-Term Baby Monitor Security
Regular Maintenance Routines
Effective baby monitor security maintenance requires consistent attention to device management and baby monitor security monitoring practices:
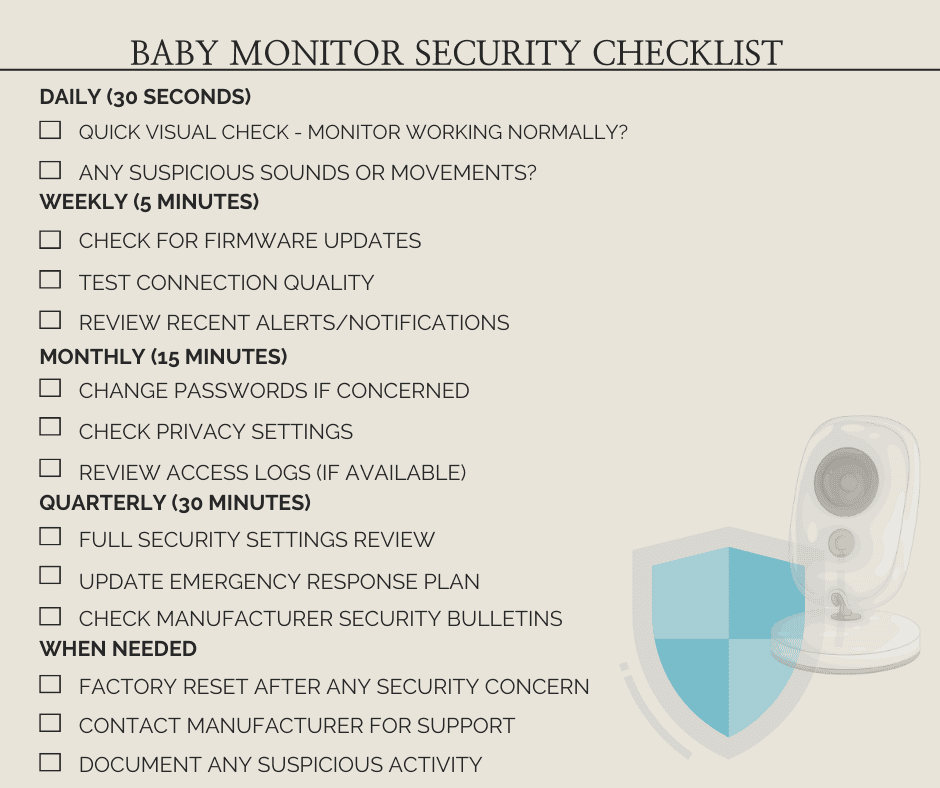
Weekly Security Tasks:
- Check for available firmware updates
- Review recent access logs (if available)
- Verify all security settings remain properly configured
- Test basic monitor functionality
Monthly Security Reviews:
- Audit user accounts and permissions
- Review network access logs
- Update passwords if concerned about exposure
- Check manufacturer security bulletins
Quarterly Deep Security Audits:
- Comprehensive baby monitor security assessment
- Network vulnerability scanning
- Review privacy settings and data retention
- Evaluate need for security upgrades
Staying Informed About Emerging Threats
The baby monitor security landscape evolves rapidly as new baby monitor malware protection challenges emerge. Stay informed through:
Manufacturer Communications Subscribe to security alerts from your device manufacturer to receive timely notifications about baby monitor protective measures updates and security patches.
Industry Security Resources Follow cybersecurity organizations that monitor IoT device threats and provide baby monitor security awareness updates for consumers.
Government Security Advisories The UK’s National Cyber Security Centre regularly publishes guidance relevant to consumer IoT devices, including baby monitor risk management recommendations.
Stay updated on the latest IoT security threats through resources like the SANS Internet Storm Center, which monitors emerging cybersecurity risks and provides regular updates on new vulnerabilities affecting connected devices.
Planning for Device Lifecycle Management
Update Support Periods Under the PSTI Act, manufacturers must clearly communicate their defined support periods for security updates. Plan device replacement before support ends to maintain adequate baby monitor security protocols.
Data Migration and Disposal When upgrading or disposing of monitors, ensure proper data deletion:
- Factory reset devices before disposal
- Verify all personal data has been removed
- Consider physical destruction of storage components for highly sensitive applications
Building a Comprehensive Family Security Strategy
Integration with Home Security Systems
Your baby monitor security configuration should complement broader home security measures:
Network Security Architecture
- Implement network segmentation for IoT devices
- Use enterprise-grade firewalls if budget allows
- Consider professional network security audits
- Maintain updated inventory of all connected devices
Physical Security Considerations
- Position monitors to minimize visibility from windows
- Secure device mounting to prevent tampering
- Consider backup power solutions for critical monitoring
- Implement physical access controls for network equipment
Education and Awareness
Family Security Training Ensure all family members understand baby monitor security guidelines:
- Recognize signs of potential compromises
- Know how to respond to security incidents
- Understand privacy implications of connected devices
- Practice good password hygiene across all accounts
Staying Current with Threats Security threats evolve constantly, making ongoing education essential for maintaining effective baby monitor security awareness.
Conclusion
Protecting your baby monitor from hackers requires understanding the risks, implementing proper security measures, and maintaining vigilant monitoring practices. The UK’s new Product Security and Telecommunications Infrastructure Act provides important baseline protections, but parents must remain proactive in securing their devices.
Remember these key baby monitor security best practices:
- Change default passwords immediately and use unique, strong credentials
- Enable all available security features and keep firmware updated
- Monitor your network for suspicious activity
- Consider DECT-based alternatives for maximum security
- Implement comprehensive network security measures
- Stay informed about emerging threats and security updates
Your baby’s safety and your family’s privacy depend on taking baby monitor security seriously. While the technology offers tremendous peace of mind when properly secured, compromised devices can expose your most private moments to strangers.
For specific product recommendations and detailed comparisons of the most secure baby monitors available in the UK, check out our comprehensive guide to the best baby monitors for British families.
Don’t let security concerns prevent you from enjoying the benefits of modern baby monitoring technology. With proper precautions and ongoing vigilance, you can maintain both convenience and security for your growing family.
Additional Resources:
- Best Baby Monitors for Large Houses – Security considerations for extended range monitoring
- Best Baby Monitors with Two-Way Talk – Securing interactive communication features
- Best Baby Monitors for Twins – Multi-camera security setup
- Best Portable Baby Monitors for Travel – Maintaining security away from home
- Best Baby Monitors Without WiFi – Maximum security options
- How to Set Up Baby Monitor in UK Homes – Step-by-step security configuration
Frequently Asked Questions
Q: Can baby monitors really be hacked?
A: Yes, baby monitor hacking is a documented security threat affecting thousands of devices worldwide. Internet-connected monitors are particularly vulnerable to cyber attacks if not properly secured.
Q: How do I know if my baby monitor has been hacked?
A: Warning signs include unexpected camera movement, strange voices or sounds, settings changes you didn’t make, and unusual network activity. If you notice any of these signs, disconnect the device immediately.
Q: Are DECT baby monitors more secure than WiFi monitors?
A: DECT technology generally offers better security because these devices don’t connect to the internet and use dedicated frequencies with built-in encryption. However, properly secured WiFi monitors can also be very safe.
Q: What should I do if I think my baby monitor is hacked?
A: Immediately disconnect the device from your network, power it off, change all passwords, update firmware, and consider factory resetting. Document any evidence and contact authorities if you suspect ongoing surveillance.
Q: Do I need to worry about baby monitor security with basic audio-only monitors?
A: Audio-only monitors, especially DECT-based models, generally present lower security risks than video monitors. However, any device that transmits data wirelessly requires basic security precautions.
Q: How often should I update my baby monitor’s security settings?
A: Check for firmware updates weekly, review security settings monthly, and conduct comprehensive security audits quarterly. Always update immediately when manufacturers release security patches.




